What is authorization, how does it differ from authentication or identification
How to design an authorization block so that users feel comfortable
We pay on the Internet, buy and sell, leave sensitive data, open many accounts. This is how users behave when they visit the sites of our projects. Accordingly, we need to confirm that the user is the one who has permission to perform certain actions. So, let's look at the tools that can be used to authorize a user on a site.
What is authorization, how does it differ from authentication or identification
To begin with, let's define terms. Identification is defining who we are. How to recognize a person on the street. Authentication (verification) is a confirmation that this person is who they say they are or who we think they are. In ordinary life, documents are shown for this. And authorization is the granting of confirmation to a person of the right to certain actions, access to information, etc. On sites, all three processes usually take place at once, they are not separated in time.
They usually talk about authorization, because interactions on the network are always about granting certain rights - to view content, edit it, make payments, etc.
Read also: How to find out the CMS of a site: an overview of analysis methods
What is authorization and how does it work?
Authorization is a method of protection. It defines the rights of users in such a way that they will be different: some can log into the account/send messages/use the device, some can edit the content, and some cannot. In order to determine who has this or that privilege, authentication is carried out - the user is defined as having the right to certain actions.
In a broad sense, authorization is, for example, a key to a room that is provided after settling in a hotel. On the Internet, this is the process of verifying the user and granting him certain rights. If we consider what authorization is from the point of view of the process, then:
the system receives a request to perform certain actions;
authenticates the user as having or not having the right to them;
satisfies or rejects the request (misses to the mailbox, work account, banking application, etc.).
What types of authorization are currently used
Certain services allow you to log in using a third-party verified account — for example, Google, Facebook, Twitter, etc. These systems are believed to be quite secure, but accounts in them are regularly hacked.
The simplest type of user authorization, which is familiar to everyone who has at least once had an e-mail, is a login and password. This is common, but this is where the benefits of such authorization end. In return:
passwords are often lost;
the password is easy to crack or steal through phishing and other methods.
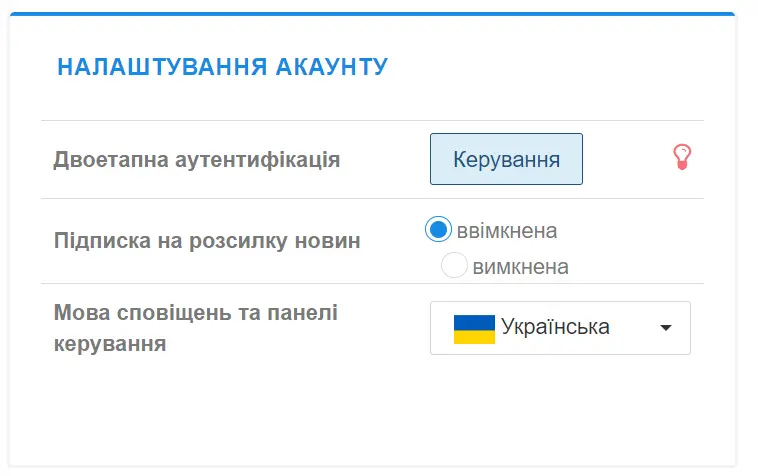
Therefore, as a rule, two-factor authorization is added - for example, after entering the correct password, the phone receives an SMS or a call, or you have to answer a control question, etc.
By the way, two-step authentication for logging into your account is also available on the Cityhost.ua website. It will help protect your hosting , domains, rented VPS and dedicated servers from hackers. Read instructions on how to enable two-step authentication .
Types of authorization that are used most often:
Client authorization through a third-party service (google account, social network account, phone);
Authorization by mail (a letter with a one-time password is sent to the e-mail;
Authorization via SMS;
Authorization by call;
Creation of a login token (exchange of encrypted messages).
Such authorization requires the user to perform an additional action to enter his account.
Services and tools for authorization
The simplest services allow you to identify and admit a user to the system by email. But this is obviously not suitable if you plan to receive payments through the site - for example, if it is an online store. Sites for which the security of their users' data is important perform more complex verification using a one-time code by mail, SMS or call, for which they use specialized services or tools. Let's figure out what they are.
Out-of-the-box solutions based on the popular WordPress and PrestaShop engines
The Wordpress engine offers several plugins that enable two-factor authentication and user authorization:
Two-Factor WordPress is a free plugin that sends one-time codes to email;
The Gateway API allows you to send SMS simply from the site admin, as well as arbitrarily format these messages, in particular, add a user name, etc.;
Rublon allows you to use both SMS and e-mail codes and other methods.
We wrote about the protection of sites on Wordpress and, in particular, about security plugins. Some of them also allow two-factor authentication.
The Security Pro module for the Prestashop engine, on which online stores are built, also allows you to enable two-factor authentication.
Read also: CRM systems — what they are, why they are needed and which one to choose
Services for authorization by SMS — Kyivstar, Messedo, Decision
Authorization via message assumes that the user enters a password or enters the site in another way, and then the system sends him a code via SMS. The code is entered in a special field on the site or it is inserted automatically.
One of the largest operators providing such services is Kyivstar. The mobile operator offers the possibility of sending a wide variety of messages for business, including for verification.
Specialized SMS-only services offer two-factor authentication through messages to the phone, classic SMS or Viber. For example, Messedo offers to pay less than a kopeck for a message in the messenger, while a classic message will cost 58 kopecks. The code is received in the message, the client enters it on the website and enters his account.
And here is another similar service, more discreet — Decision. It also refers to mass SMS mailings, for example, for advertising, to confirm orders, etc. And SMS for two-factor identification is one of the services. By integrating this protocol on the site, you can also send SMS to confirm transactions.
The services are connected to the site using the SMS API, protocols that allow you to integrate SMS messaging into existing software and do everything quickly.
The plus of such services compared to CMS plugins and modules, which allow you to send SMS simply from the site admin, is that you can be contacted by a specialist who will quickly sort everything out if something goes wrong.
Services for authorization by call — Zadarma, ITTel, AlphaSMS
This method of verification is widely used, for example, by "Privatbank". Authentication methods can be different. Somewhere you have to answer the call and press certain numbers, somewhere - simply accept it, somewhere - enter the last digits of the number from which the call just came on the website.
Call-in phone number authorization has two advantages:
the call arrives faster and practically does not get lost, unlike SMS;
the call is cheaper;
the call is believed to be more difficult to intercept.
There is an open API for such authorization on the well-known Zadarma service. This is a cloud telephony service. By creating a virtual number and integrating the protocol on your site, you can make verification calls with the code. You just need an employee who can correctly integrate the code, or some time to figure it out.
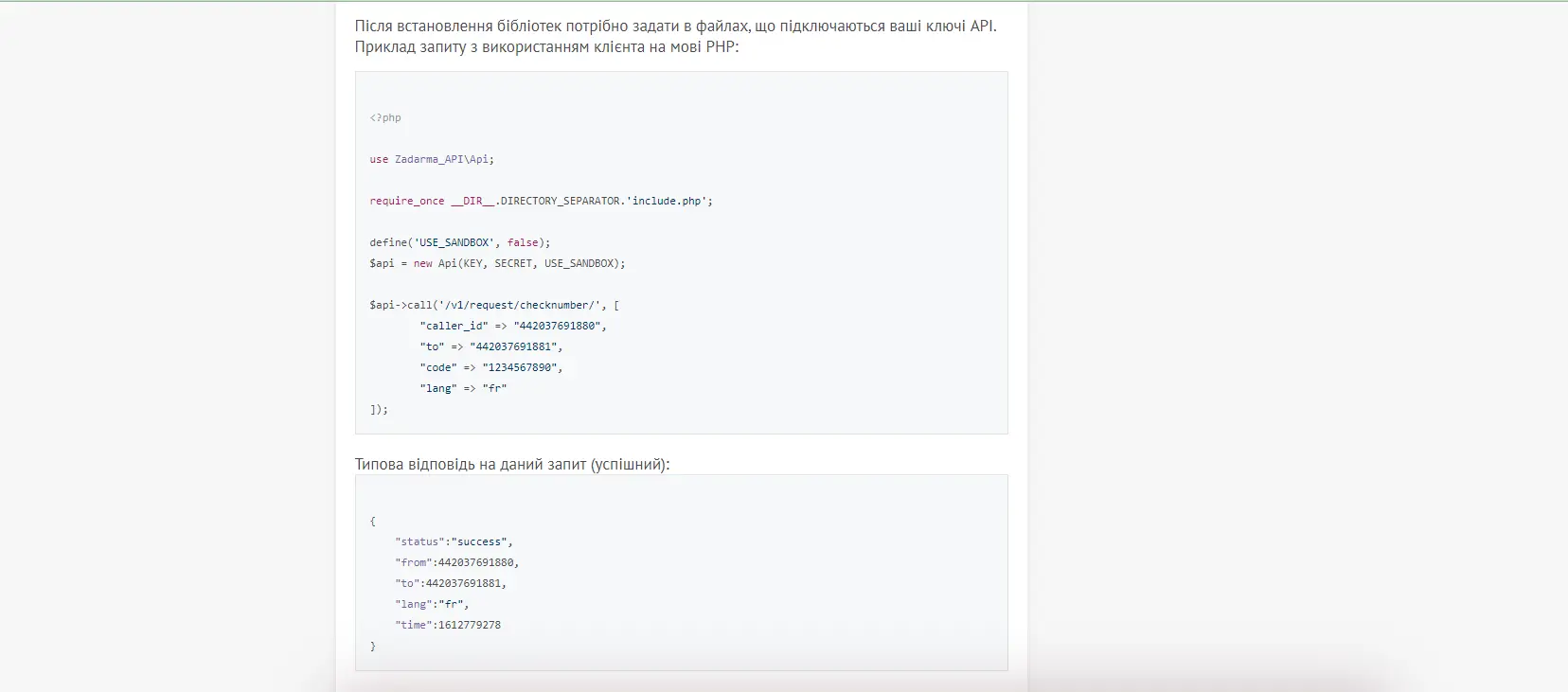
There are services that offer to do everything for the client's money.
Call authorization in ITTel, for example, is possible both from the website and from the mobile application, can be integrated with CRM and the loyalty system.
And AlphaSMS will immediately give a free widget, so as not to involve programmers.
Most services offer free testing.
Read also: How to create your website for business: independently, easily and relatively cheaply
How to design an authorization block so that users feel comfortable
The main principle is to be clear and not distract the user from the main goal. If you authorize the client anyway, you should not offer him a captcha, guessing pictures or any other quests. If possible, you can even avoid entering both the password and the SMS code at the same time. Authorization is an additional step in the process, and modern people are always in a hurry and don't like to stop.
The clearer the authorization field, the more concise and unambiguous, the better they react to it.
In particular, it should be:
large enough for the information that is entered there;
contain only one clear button, a clear call to action, a minimum of other details;
preferably placed so as to attract attention. Nothing is more confusing on the website of Kharkiv Heat Networks than searching where to log in to transfer indicators.
There are many ways to make input more pleasant and attractive:
a string that responds to input;
contrast button that responds to pressing;
a concise and clear message about what to expect after entering data (you will be directed to the site, an SMS will be sent to the phone, a letter will be sent to the post office, etc.);
a convenient error message if the client made one;
auto substitution of the code if an SMS arrives.
In general, you should mentally go through the entire authorization process several times from the client's point of view and note at which stages it becomes a bit boring or difficult for you, or if something cannot be abandoned. Then the balance between security and convenience will be as it should be - maybe not perfect, but there are few things that are perfect.
The services discussed in this article are far from an exhaustive list. However, plugins, paid services, and open APIs operate on similar principles. Therefore, it is worth choosing from the point of view of the price acceptable for the budget and, possibly, additional options that are needed in a specific situation. It is not difficult to organize two-factor authentication with their help, but it protects both the project and its customers.