A business page on Facebook is an effective way to promote your business, creativity, and personal brand. This platform does not require large financial investments or deep knowledge, which is why thousands of entrepreneurs, including beginners, use it. The main resource that needs to be invested in the development of a page is time and effort, which help it grow with subscribers. It is the audience of the page that is its main value, and it is this audience that interests scammers the most, as they seek to steal a business page on Facebook.
According to research by cyber security experts at Privacy Affairs, we found in a report from the channel '1+1' that the price of hacking one page on Facebook is $100 USD. This is the price from 2020, so it is likely that the amount is different now. But it is important to understand that pages are still being targeted. The owner of an old page has a lot to lose – reputation, a large and loyal audience, profit. Ultimately, it's a waste of their own time. Therefore, it is important to follow simple rules to prevent this from happening.
Why scammers hack Facebook pages
Firstly, anyone who has ever developed a page knows how difficult it is to build an audience and earn a reputation. Therefore, a popular page is a valuable find for anyone who would like to gain an audience quickly and effortlessly.
So, how can scammers use stolen pages:
-
Sell to other business owners in similar niches to quickly start selling to an already warmed-up audience.
-
Disrupt competitors' work — retrieving stolen work is difficult and can take weeks. Such an attack can disrupt a small business to the point where it may take a long time to recover.
-
Change the page's name and promote messages among the appropriate audience that has already been gathered. This can be anything from self-promotion to Russian propaganda messages. The latter are actively promoted from pages originally focused on innocent themes such as life stories, crafts, and jokes. Periodically, waves of paid advertising are launched from them. By the way, money in the advertising account is also stolen along with the page.
-
Promote other pages or Telegram channels: in the example above, you need to switch to Telegram.
-
Spread links to hack other pages — links supposedly for promotions to steal card details or other sensitive information.
-
In some cases, they may demand ransom from you — either to actually get money or to lure out card details.
In short, all the goals are malicious — unfair competition, spam, phishing, personal data theft, and direct work against the owner.
Read also: Fakes and disinformation: learning to recognize false information on the Internet
How page hacking occurs
Recently, many owners of business pages on Facebook received messages allegedly from the social network's administration. These messages demanded clicking on a link, otherwise the page would be supposedly blocked. At first glance, the link may have seemed harmless — verification, what's the big deal?
But have you ever seen Facebook admins with usernames like StandardViolate or HealthAppealCopyright? It's worth taking a minute to check the page that sent the message. And here's what we'll see: in the past, it was a children's clothing store. And even from the photo history, we can guess at what point it was hacked.
Most likely, the hack occurred in the same way, after which the photo was changed, and the scammers started sending messages from the page's name to others.
There are many ways to gain access to other people's pages: from technically simpler to more complex. When scammers try to gain access to other accounts, they can use several methods. For example:
-
Social engineering. These are well-known methods of influencing people using psychological techniques. For example, a call claiming to be from security services or an advertising agency urgently requesting verification of data, providing a password for the account, or a secret code.
-
Keyloggers. These are applications that remember keyboard and mouse movements, thus capturing passwords. A keylogger can be accidentally obtained through the Internet or with the help of an infected flash drive.
-
Phishing. This is a very common hacking method, an example of which we just mentioned: a user receives an email or a message (or a message from a business page) containing a link that appears to be safe, but when clicked, it leads to a login page identical to the real one. By logging in through it (for example, to allegedly confirm ownership of the page), the user hands over their login and password to the scammers.
-
Session data theft. Hackers can steal cookies, i.e., login data saved in the browser. Sometimes this is more difficult, and sometimes easier, because we may inadvertently store login data on a shared computer or on a public network.
-
Browser hijacking and password manager data theft.
-
Hacking email accounts, where information about social networks can be obtained.
-
Viruses, botnets, DNS attacks. All these methods are more expensive and complex, but sometimes they are used. For example, there are viruses and worms that not only disrupt the infected computer's operation but also can provide hackers with access to passwords.
However, as we can see, the cheapest and simplest methods, and therefore the most common ones, are based on the hope that the user will click somewhere without thinking or will disclose sensitive information to someone. Because the responses are requested as quickly as possible — urgently, right now — while trying to induce panic and disorientate the person with unpleasant prospects. Therefore, the majority of protection methods involve slowing down a bit and not reacting based on emotions.
How to protect your Facebook business page from scammers
First of all, it is worth internalizing and teaching your employees elementary security rules:
-
Don’t click on suspicious links and do not open any links from unfamiliar people. Suspicious links can also be sent by acquaintances if their accounts have already been compromised. Therefore, if you receive a link in a message without context or with a strange message, it is better to ask what it is.
-
Download software only from trusted publishers.
-
Use only clean and verified flash drives.
-
Don’t give out passwords to anyone.
-
Clear your browser history and do not store passwords in a password manager.
-
Don't give people you do not trust access to your phones, laptops, and other devices.
-
Don’t use personal Facebook pages, which are linked to business accounts, to participate in games and tests ("what color flower are you", "what will you look like in ten years", and the like) if it requires giving the game or test app access to your profile. This can also be a way to hack a page.
-
It is advisable to have multiple admins on one business page so that in case of problems with one account, another administrator can quickly remove them from management — before anything happens.
In general, this applies not only to Facebook: if you are persistently and urgently asked to do something online, it is better to stop and think.
It is also important to protect your email, as a significant number of hacks occur through it. The rules are similar—do not give out your email to anyone and regularly change your password, do not open links from unfamiliar addresses (and preferably from familiar ones if the email only contains an unclear link).
Additionally, there are additional security measures you can take.
Read also: How to create a business page on Facebook
Secure passwords that are regularly updated
In reality, the battle between convenience (after all, we all risk forgetting/losing our password) and security is eternal. However, it is important to overcome this and regularly change your passwords, as well as make them less obvious and easy to guess. You can use password generators such as LastPass, Delinea, and so on.
Two-factor authentication
This feature, as well as the ones mentioned below, is available on personal pages. However, since they are used for administering business pages, it is important to ensure their reliable protection.
The essence is that after you enter your password, the system sends a one-time code to you via SMS or calls you. This feature is available in many social networks — including Facebook and Instagram.
In the browser version of Facebook, setting up two-factor authentication starts with entering settings (top right corner, where your profile picture is: a menu will drop down, and you need to select "settings").
In settings, you will find the Meta account center.
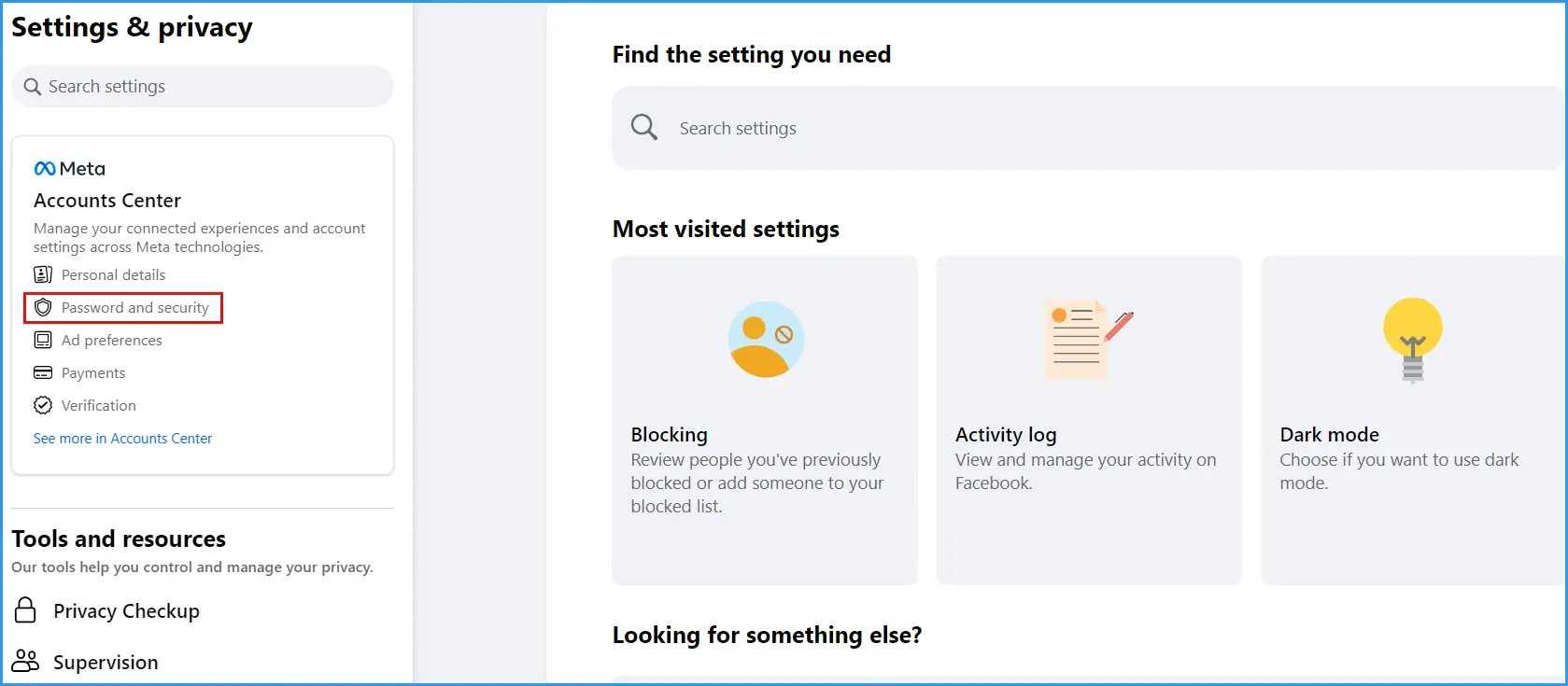
Next, go to the "password and security" tab and look for the two-factor authentication menu. You can protect several accounts. Read more about two-factor authentication here.
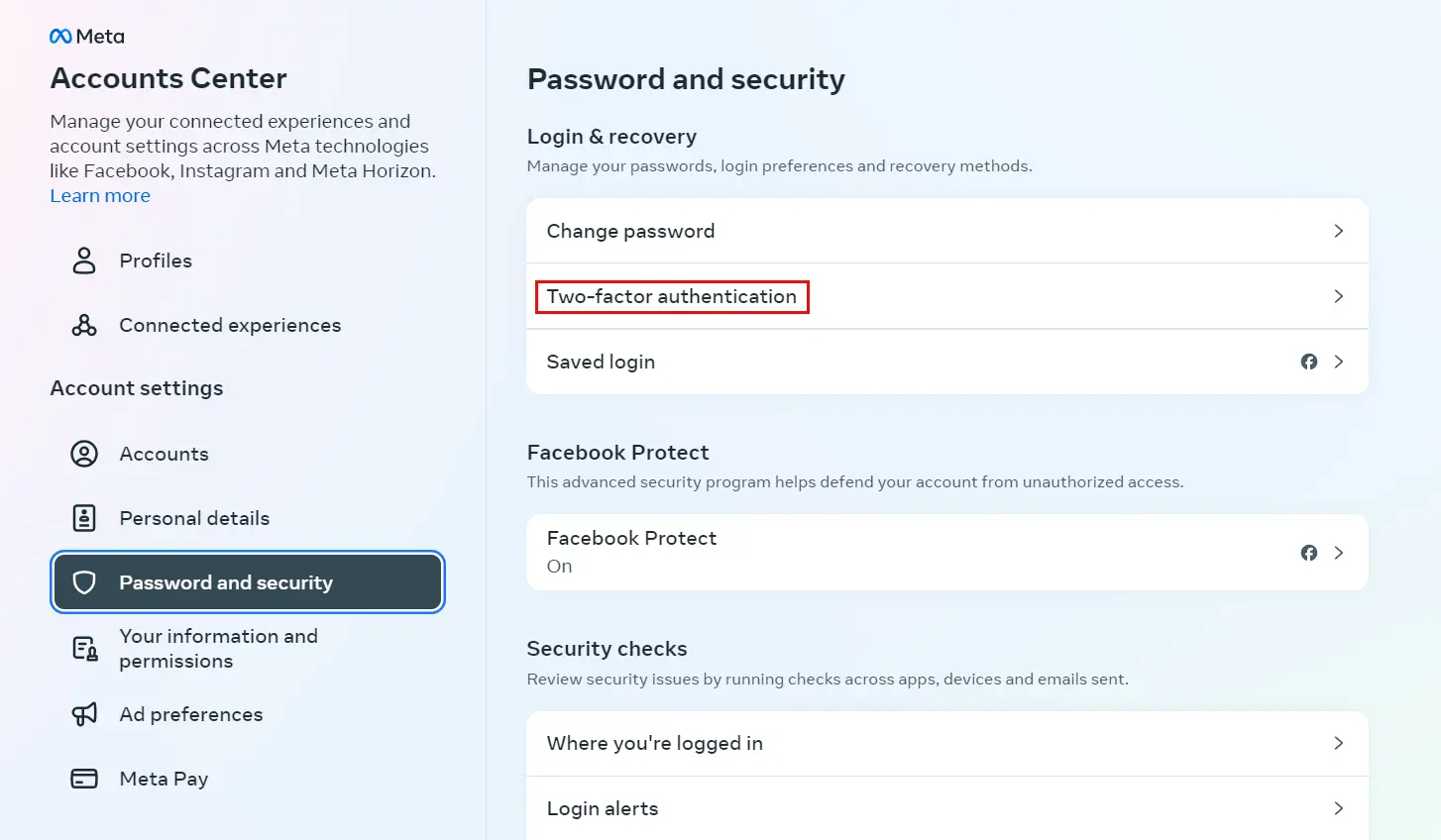
With the help of two-factor authentication, you can protect not only pages in social networks, but also domains, hosting for websites, DS and VPS servers in the Cityhost account. You can read about this and other methods in the article How to protect your Cityhost account in times of information instability.
Authenticator apps
In particular, we are talking about Google Authenticator, Microsoft Authenticator. These are also applications that you download to your phone. They connect, in particular, to MetaBusiness and allow you to set up reliable verification with regular code changes.
There are also apps that use biometric data and FaceID. Their problem is that the camera may not always accurately transmit appearance in different lighting conditions, and, for example, fingerprints can change significantly as a result of burns or other injuries. However, this is a fairly reliable method.
Physical key
A physical key resembles a flash drive, and you also need to connect it to your computer through a port to gain access. Essentially, this is also two-factor authentication, but very specific, because to enter somewhere, you need not only to know the login, password, but also to have a physical device for entry. You can read more about this by following the link.
It is also very important to monitor activity in your account: suspicious actions or messages from the system about logging in from another city may indicate that there has been at least an attempt to hack. In this case, it is better to log out of all sessions on all devices and urgently change passwords. It should be added that geolocation is not always as accurate as we would like. Therefore, we know stories of people who blocked access to themselves, only on another device, because the system mistakenly believed their location to be kilometers away from the city where they actually were.
What to do if your Facebook page is hacked
Unfortunately, regaining access to a hacked page takes some time. Facebook has an option to report page theft.
When hackers hack a page, it may be accessible to admins — the scammers try to make it so that the owners do not notice the hack. If you suspect a hack, use this form to contact the administrators and protect the page.
Or the page may be inaccessible for login — this is already a complete theft. There is also a scenario where your private page is hacked, and then your business page along with it. For such cases, Meta has the option to file a complaint regardless of whether you can log in.
You need to visit the Meta account center and inform the admins that your page has been hacked. The system can apply various verification methods — use those email addresses that you have access to, send an SMS, suggest marking trusted contacts for future access recovery.
At the same time as filing a complaint, you can also contact Facebook support, describing the problem.
If you have any uncompromised accounts that can communicate with customers on your behalf, it makes sense to file a report. Inform them that you have become a victim of scammers and are working to regain access to the pages. This will help minimize the consequences to some extent.
After your page is, hopefully, restored, it is worth reviewing the security policy regarding your business and personal accounts.
Finally — about page cloning as one type of fraud
In addition to everything listed, one more type of fraud should be added, which does not involve the theft of personal data or, in fact, the page itself. Scammers create complete clones of existing pages, and use them to sell their products, deceive users, and so on.
This type of fraud cannot be prevented, but the damage from it is much less: your page remains with you. However, it can cause reputational damage. Therefore, if you find something similar on the internet, try to do two things:
-
Report the page as a fake profile.
-
Notify your audience about the clone to protect customers from the threat. In addition, you will receive a certain number of people who are friendly to you and have a sense of justice, who will also file a complaint, so there is a chance that it will be reviewed and satisfied faster.
There is no way to completely protect yourself from scammers, but caution on the internet can significantly reduce their chances of harming you.