
- What is the TLS protocol and what do versions 1.0, 1.1, 1.2, and 1.3 mean
- A brief history of TLS development
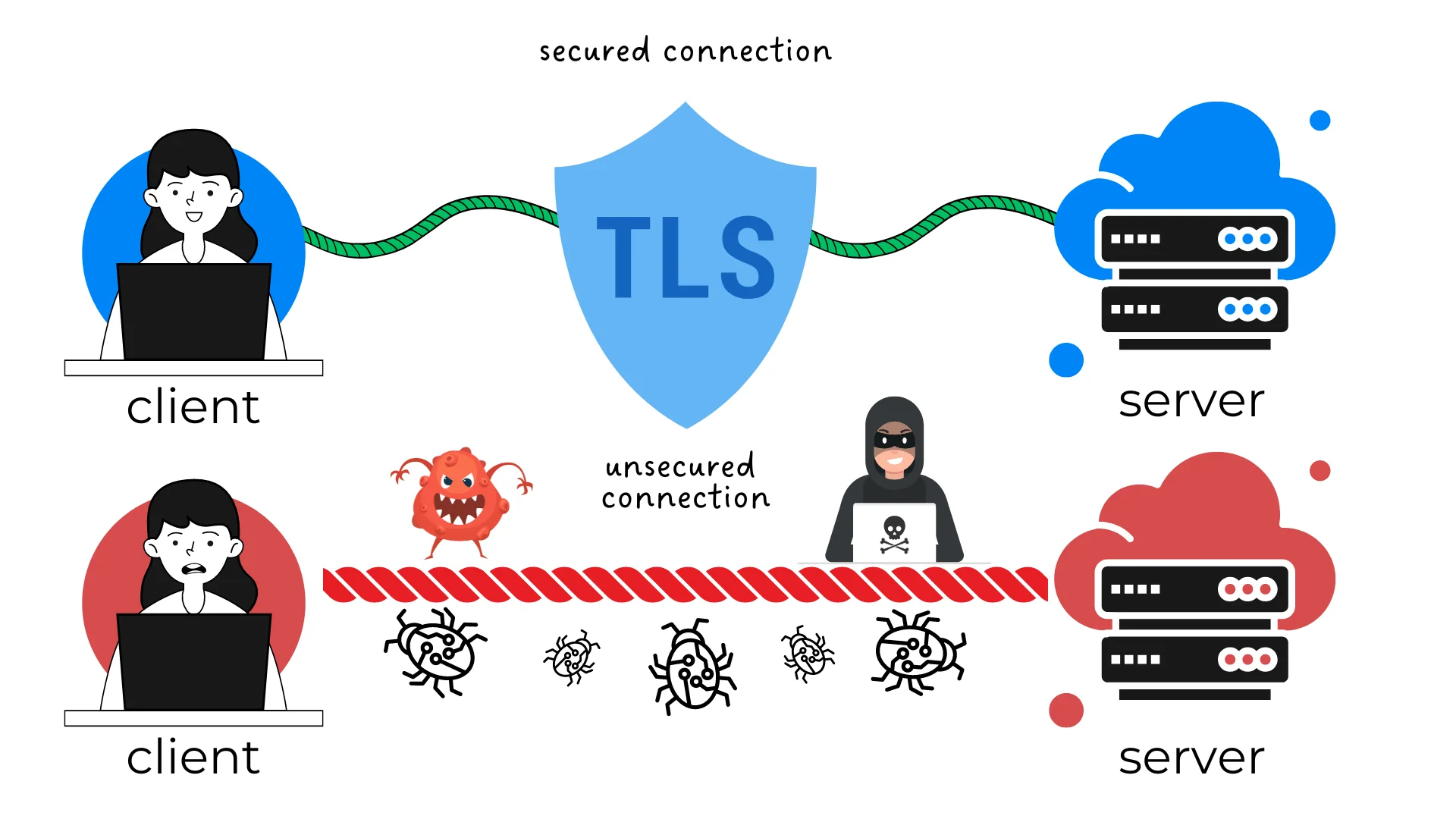
- What data does the TLS protocol protect
- How TLS protocols work
- How the TLS protocol is used in hosting provider services
- Cyber threats that TLS protects against
- Popular Security Tests for Websites
In the vast world of the Internet, where we search for information, communicate, and make purchases, the security of our personal data is crucial. One of the main tools for protection is the TLS protocol.
Let's take a closer look at what TLS protocols are, how they have evolved over time, and become an integral part of our digital lives. We will also discuss industry issues — how the TLS protocol is used to enhance the security of virtual hosting services, as well as other services and tools provided by hosting providers.
What is the TLS protocol and what do versions 1.0, 1.1, 1.2, and 1.3 mean
TLS (Transport Layer Security) protocols are cryptographic protocols, special rules that help protect the privacy and security of Internet users. They make the information transmitted over the Internet inaccessible to attackers.
The abbreviation TLS stands for Transport Layer Security. It's important to know that TLS is a kind of "code" for data protection. When you use the Internet, your data travels through various networks where hackers may be present. TLS helps encrypt your data, making it difficult for hackers to understand.
TLS works like an invisible "protocol envelope" that wraps the data so that only the sender and the receiver can read it.
Now, about the numbers. TLS 1.0 and 1.1 are older versions of this protocol, while 1.2 and 1.3 are more recent. As with all technologies, better and more secure versions emerge over time.
Currently, TLS 1.3 is the most relevant and widely used version of the protocol. All previous versions (SSL, TLS 1.0, TLS 1.1, TLS 1.2) are considered outdated.
Support for older versions of TLS (1.0 and 1.1) is being discontinued. This means that programs or systems using these protocol versions may lose connection with servers or services requiring newer versions of TLS. Therefore, it is recommended to update systems and programs to support TLS 1.3.
The predecessor of TLS was SSL, which has long been considered insecure and is no longer supported.
By now, you may be thinking: wait, if the SSL protocol is outdated and not used, why do SSL certificates, which are mandatory for websites, still exist?
The term "SSL certificate" became standard in the field when SSL was first introduced. Although certificates for TLS connections are now used, the term "SSL certificate" remains in use due to its historical prevalence and user familiarity. Essentially, modern SSL security certificates are actually certificates used to secure TLS connections.
Read also: What is an SSL certificate, why do you need one and how to choose one
A brief history of TLS development
When the Internet was just beginning to be widely used, people realized that transmitting data over the network could be dangerous. The solution to this problem was the development of SSL — Secure Sockets Layer — by Netscape Communications. SSL first appeared in 1994, and the following year, in 1995, SSL 2.0 was released, becoming popular among websites and browsers.
However, over time, it became clear that SSL had its vulnerabilities, so specialists began working on improvements. In 1999, TLS 1.0 appeared, based on SSL 3.0, and it was standardized by the Internet Engineering Task Force (IETF). The new protocol began to be used to create secure connections between clients and servers on the Internet.

Later, in 2006, TLS 1.1 was introduced, addressing some of the shortcomings of TLS 1.0. In 2008, TLS 1.2 was released, bringing even more improvements in connection security. However, development did not stop: in 2018, TLS 1.3 was introduced, becoming the latest version of the protocol with significant changes in speed and connection security.
Read also: What is a Domain and How is it Different from Hosting
What data does the TLS protocol protect
Let's take a closer look at the specific purposes of the TLS protocol and the types of criminal actions it protects user information from.
- Protection of data privacy. TLS encrypts the data transmitted between the client and the server, making it unreadable to any third parties trying to intercept the information for their own purposes. Only authorized users can access this data.
- Ensuring data integrity. TLS includes mechanisms for verifying the integrity of data during transmission. This helps detect any attempts to alter or damage the data while it is being transferred.
- Server authentication support. TLS helps ensure that you are communicating with the server you intended to interact with. This is achieved through the use of certificates that verify the server's authenticity, helping to prevent attacks aimed at server impersonation.
- Prevention of data interception and forgery. TLS helps prevent the interception of data during transmission over the network and protects against its forgery.
How TLS protocols work
In this section, we’ll explain in simple terms how TLS protocols work and what happens behind the scenes. This is a step-by-step process that occurs very quickly — for example, establishing a TLS connection typically takes about 100-300 milliseconds.
- Connection establishment. The first step is to establish a connection between the user’s device and the server. The client sends a "ClientHello" message to the server, specifying supported versions of the TLS protocol, a set of cryptographic algorithms, and other parameters. The server responds with a "ServerHello" message, selecting the parameters.
Simply put: imagine you want to talk to a friend through an encrypted communication channel. First, you need to agree on how exactly you’ll do this. It’s like choosing a language you’ll both speak. Once you’ve selected encryption methods, it’s time to exchange keys. The client and server exchange these keys to ensure the security of their communication. - Authentication of parties. The server sends a certificate to the client for authentication. If the client also needs to authenticate, it sends its certificate in response. At this stage, the client ensures that it is communicating with the intended server, not an imposter — and vice versa, the server confirms that the client is who they claim to be.
- Key generation. The client and server generate a shared secret key using a key exchange protocol, such as Diffie-Hellman. Asymmetric encryption is used to securely transmit this key. Here, different keys are used for encryption and decryption: one public, the other private.
- Encryption and data handling. Once the client and server trust each other, they begin exchanging data. All data is encrypted so that no unauthorized party can read it. Symmetric encryption is used for this, where the same key is required for both encryption and decryption.
- Connection termination. When all necessary communication is complete, the client and server close the connection. They stop exchanging data and terminate the communication channel.
Read also: What is robots.txt and how to configure robots.txt for WordPress
How the TLS protocol is used in hosting provider services
In hosting provider services, TLS is used to protect the transmission of data between users and servers.
Encryption of website traffic
TLS is used to encrypt data transmitted between users' web browsers and web servers. This is achieved through the use of HTTPS, which is the secure version of HTTP.
How it works:
- SSL/TLS certificates: Hosting providers offer SSL/TLS certificates that can be installed on web servers.
- Automatic HTTPS support: Many hosting providers offer the option for automatic installation and renewal of SSL/TLS certificates, for example, through Let's Encrypt.
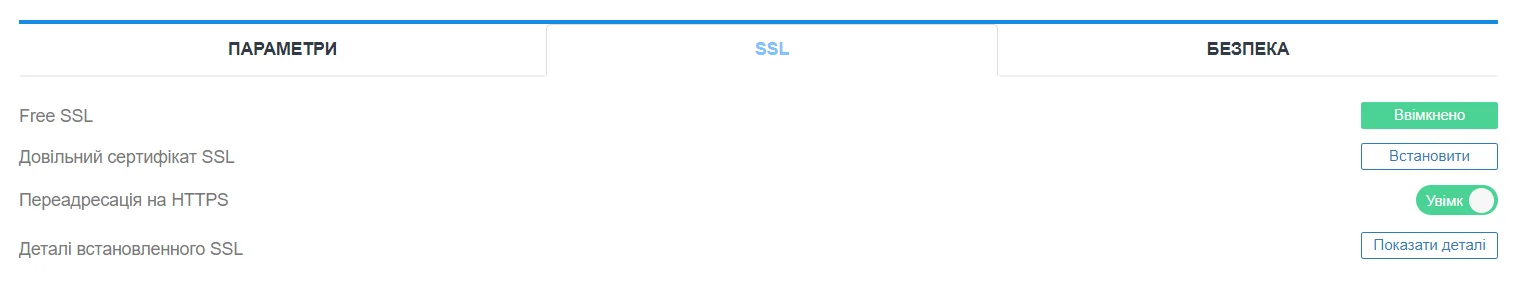
Specifically, at Cityhost, you can install a free SSL certificate and enable HTTPS redirection via the control panel in just two clicks. We also offer paid certificates with different levels of protection.
Read also: How to Adapt Your Website for Mobile Devices
Email Protection
TLS is also used to encrypt email traffic.
How it works:
- SMTP over TLS (SMTPS): Mail servers use TLS to encrypt connections when sending emails via the SMTP protocol.
- IMAP/POP3 over TLS: Incoming emails are protected through encrypted connections when using the IMAP or POP3 protocols.
FTP and Other Service Protection
For secure file transfers between users and servers, secure versions of protocols such as FTPS (FTP Secure) or SFTP (SSH File Transfer Protocol) are used.
How it works:
- FTPS: Uses TLS to encrypt connections between an FTP client and server.
- SFTP: Uses SSH for security but is also commonly offered by hosting providers for secure file transfers.
Read also: SPAM: why emails end up there and how to avoid it
Control Panel Protection
Hosting providers use TLS to secure connections to the hosting control panel. This ensures that users can safely access their accounts and data.
Cyber threats that TLS protects against
There are many cyber threats on the internet that the TLS protocol protects against:
- Man-in-the-Middle Attacks. This is an attack where an attacker intercepts and potentially alters the data transmitted between you and the server.
- DNS Spoofing (DNS Cache Poisoning). Attackers can spoof DNS records to redirect you to fake sites, even if you enter the correct website address. When connecting to a site via HTTPS, the browser checks the server's certificate. If the certificate does not match what is expected, the browser warns you of potential danger. This helps identify fake sites, even if they use the correct domain name.
- Session Hijacking. An attacker intercepts your session with a website after authentication, allowing them to act on your behalf. TLS encrypts all traffic, including session cookies. This complicates the attackers' ability to intercept and use your session data.
- Data Tampering. An attacker may alter the data being transmitted between you and the server. For example, they could change the transaction amount during online payments. TLS ensures data integrity through message authentication mechanisms (MAC).
- Replay Attacks. An attacker intercepts and resends your previous successful transaction to try to carry it out again. TLS uses unique session numbers and timestamps, making it difficult to reuse intercepted data.
- Eavesdropping (Sniffing). Attackers can use special tools to intercept your traffic and read unencrypted data, such as passwords, credit card numbers, and personal messages. TLS encrypts all traffic transmitted between your device and the server, making it impossible for attackers to read.
- Man-in-the-Browser (MitB). An attacker uses malware to inject malicious code into the victim's browser. This allows them to alter transactions without the user’s knowledge. While TLS cannot prevent the installation of malware, it complicates the interception and manipulation of data transmitted over a secure connection, reducing the effectiveness of such attacks.
- Cross-Site Scripting (XSS). Attackers inject malicious scripts onto a website that execute in the victim's browser. This script may steal cookies or other sensitive data. Although TLS does not directly protect against XSS, it encrypts cookies and other sensitive data, reducing the risk of theft even if an XSS attack is successful.
- Downgrade Attacks. Attackers attempt to force your browser to use older, less secure versions of protocols to connect to the server. Modern implementations of TLS include mechanisms to prevent downgrade attacks (e.g., HSTS - HTTP Strict Transport Security), ensuring that browsers only use secure connections.
Popular Security Tests for Websites
Protecting websites is a critical task in the modern internet, where cyber threats are constantly evolving. One way to achieve this is by conducting regular security tests. Such tests help identify vulnerabilities before they can be exploited by attackers.
Penetration Testing
Penetration testing, or pen testing, simulates hacker attacks to uncover vulnerabilities in the website's security system. Both manual testing and automated tools — specialized programs for scanning and testing various parts of the site — can be used for this purpose.
Popular Tools:
- Metasploit: A powerful platform for conducting penetration tests.
- Burp Suite: A comprehensive tool for testing the security of web applications.
Vulnerability Scanning
Vulnerability scanning tools check websites for known vulnerabilities, such as SQL injections, XSS (Cross-Site Scripting), misconfigured servers, and more.
Popular Tools:
- Nessus: One of the most popular vulnerability scanners.
- OpenVAS: An open-source solution for vulnerability scanning.
SQL Injection Testing
SQL injection tests involve attempting to input malicious SQL queries through data input forms or URL parameters.
Popular Tools:
- sqlmap: An automated tool for detecting SQL injections.
- Havij: A tool for automating SQL injections.
XSS (Cross-Site Scripting) Testing
XSS tests involve attempts to inject malicious scripts through data input forms, URL parameters, or other methods.
Popular Tools:
- OWASP ZAP (Zed Attack Proxy): A tool for testing the security of web applications, including XSS.
- XSSer: A specialized tool for detecting XSS vulnerabilities.
CSRF (Cross-Site Request Forgery) Testing
CSRF tests involve attempts to make users perform unwanted actions without their knowledge.
Popular Tools:
- Burp Suite: Contains tools for testing CSRF.
- OWASP CSRFGuard: A tool for protection against CSRF attacks.
Security Configuration Testing
Configuration testing tools check the settings of web servers, firewalls, databases, and other components for dangerous configurations.
Popular Tools:
- Lynis: A security auditing tool for systems based on Linux and Unix.
- Chef InSpec: A tool for testing and ensuring configuration compliance.
Stress Testing
This involves checking the ability of a website to withstand heavy loads and DoS (Denial of Service) attacks. Stress testing tools simulate high loads on servers to see how the system copes with a large volume of requests.
Popular Tools:
- Apache JMeter: A performance and load testing tool.
- Locust: A tool for scalable load testing.
Read also: What is a DDoS attack and how to protect your site/server
TLS plays a critical role in the modern internet by protecting data during transmission between clients and servers. In recent decades, TLS has become the standard for ensuring the confidentiality, integrity, and authenticity of information transmitted over the network.
One of the key advantages of TLS is its ongoing development and adaptation to new threats. Modern versions of the protocol, such as TLS 1.3, have significantly improved security and performance compared to their predecessors, reducing connection establishment time and increasing resilience against attacks.
However, to gain the maximum benefit from TLS, it is important to configure it correctly and keep it updated regularly. Using weak ciphers or outdated versions of the protocol can negate all the security advantages of TLS. Therefore, system administrators should closely monitor the continually evolving recommendations and best practices.











