There are many hacking technologies on the Internet. They have different goals — stealing money or data, blackmail, eliminating competitors. Most often, the motivation is reduced to illegal financial gain, but there are other reasons that push hackers to develop malicious software.
Black programmers have invented many ways to harm a web resource or server. One of the most common is a DDoS attack.
What is a DDoS attack?
A DDoS attack is a massive bombardment of a server with simultaneous garbage requests that exhaust RAM resources and completely clog traffic. The attack leads to a denial of service (Denial of Service): due to channel overload, the site stops responding to real visitors or is completely disabled. In such cases, they say: "They were knocked down by a DDoS attack."
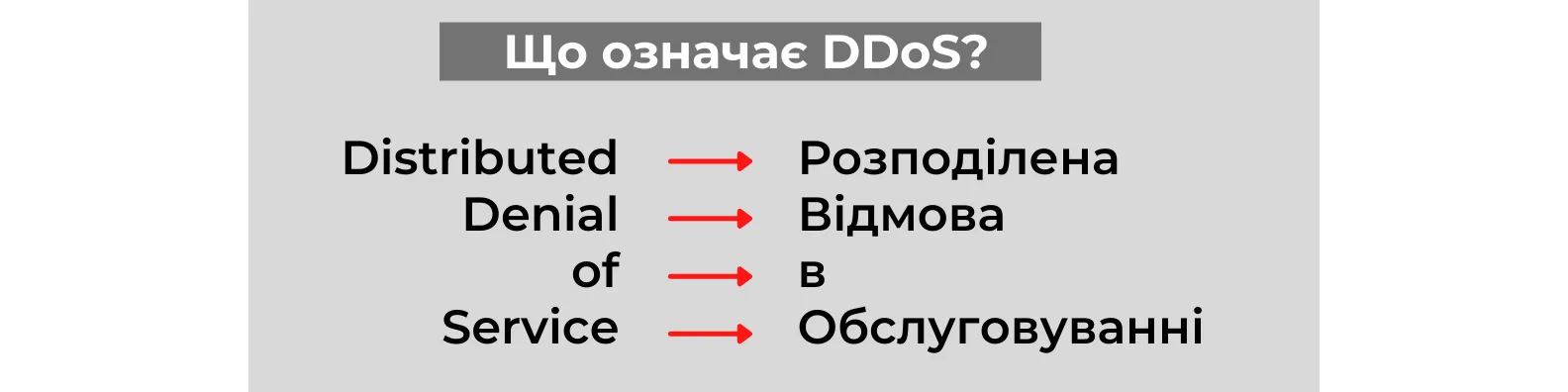
We have dealt with the denial of service, but what does "distributed" mean? So the term indicates the fact that the attack is carried out from several devices at once, it is distributed.
Sites, networks, mail services, mobile applications and other web resources can be attacked. DDoS attacks occur at all levels of network connectivity, so they have many different types and methods.
The consequences of a successful DDoS attack can be catastrophic - a drop in output due to unavailability, a complete shutdown of the server by the data center, losses due to downtime of the service, and reputational losses for the company.
Where is the attack coming from?
-
Stressors. These are special services that provide the power of their servers for a stress test on the ability to resist a DDoS attack. You just need to enter the website address, select the type of attack, pay for the service and analyze the result. Stressors are positioned as a service for testing your site and are not considered harmful. But such a service is often used by those who want to get rid of competitors. Criminals mask their IP addresses with the help of proxy servers, so there is no way to track who paid for the service and for what purpose. The power of such attacks is small, the simplest types are used. But this is enough to put a small online store. If we talk about hackers, this method is used by beginners who do not yet have enough knowledge and money for independent actions.
-
Servers. To carry out attacks, servers that were not blocked are bought or rented. Special attack software is installed on them. This is what advanced hackers are already doing. Sometimes the servers that one DDoS hacker has are not enough to put a site, and then he can turn to colleagues to help with their capacities for a certain percentage. This is how whole teams of "ddosers" can be organized.
-
Botnet. This is the most complex and powerful of all DDoS attack systems. First, you need to create an army of "zombie computers" - that's what a botnet is. This is the name given to users' devices that have been seized by attackers. The capture of control is carried out with the help of viruses that are distributed through mailings or hacked sites. The virus is embedded in the OS and allows the hacker to issue commands remotely. The owners do not even know about the illegal behavior of their computers, since the virus does not manifest itself in any way. Hackers often have a large database of such zombies, they constantly update it and periodically throw it into battle. Botnets are simply huge - up to several million machines. They live for several years, and especially large ones even have names. Maintaining such a "farm" is expensive, requires a lot of time and knowledge, so it is considered the most advanced level. Customers contact botnet owners to use their services. A DDoS attack by a botnet is expensive, but it can bring down even the most powerful web resource.
Algorithm for preparation and execution of a DDoS attack
A DDoS attack is a large-scale event that requires high-quality preparation.
Stages of attack preparation:
-
Studying the victim is gathering information about vulnerabilities that can be more effectively targeted: on which servers the site is hosted, how the code is written. Also, depending on the received data, the attack method is selected.
-
Malicious code is deployed on bot devices or servers, which will be used to carry out the attack.
-
A DDoS attack is taking place, the results are being analyzed. If it gave the expected effect, the reasons are found out. Then the attack can be repeated (and more than once).
Read also: Bad bots: how they harm the site and how to block them
Why are DDoS attacks used?
Hackers seek to bring sites and servers down for various reasons:
-
Elimination of competitors. Companies can order attacks on competitors' sites. If it is a large commercial portal, then even one day of downtime or slowdown in work leads to huge losses.
-
Blackmail. Criminals "crash" the site, after which they write or call the owners using the contact information specified on the web resource. They demand payment of a certain amount to stop the attack, which can last several days. If the company's work depends on the site, it is cheaper to pay the fraudsters, otherwise the losses will be even greater.
-
Political motives. The attack can be carried out on the websites of state organizations, political parties, individual politicians, mass media or used as a protest action.
-
Teaching. DDoS attacks require knowledge and experience, so many of them are just novice attempts by "dDosers".
-
Fun and vanity. Attacks are often carried out because of a banal desire to have fun, try their hand at it, or show colleagues what a hacker is capable of.
-
Personal motives. Any person can order a DDoS attack to their attacker. It even happened that the husband, learning about the betrayal, ordered an attack on his wife's website, through which she conducted business.
-
Internet racket. The attacker carries out an attack and turns to the owner of the site with an offer: to pay an amount every month so that the site does not crash. Otherwise, it will be attacked many times until the victim surrenders.
-
Advertising. A hacker attacks a site, then offers the owners to fix the vulnerabilities he found through such an unsolicited stress test.
How to protect your site or server from a DDoS attack
Protection is carried out from two sides - by the efforts of the webmaster himself and the provider who provided the hosting or server for rent. Therefore, it is very important to choose a service provider that guarantees high-quality protection against attacks.
Technical support of Cityhost works around the clock, organizing the security of servers and sites hosted on them. DDoS attack attempts are continuously monitored and manually remedied. If the attack is very powerful and affects the entire server, employees redirect the site to a proxy server and filter traffic on it using various methods. The data center also filters overactive DDoS protocol if the channel bandwidth is physically clogged and machine resources are exhausted.
When a DDoS attack begins on a site, our administrators notice it immediately. But if the owner sees that the site has been attacked, it will not be superfluous to notify technical support.
Each attack is unique, so support staff always act on the situation. There is no such thing as full automatic protection, all protection programs can filter only the simplest DDoS attacks. Thanks to our experience of previous years and multiple attacks, protection patterns have already been developed for certain cases, which allows us to deal with DDoS attacks very efficiently and quickly.
A real case: the owner of a web resource decided to fully protect his site using automatic methods. He hired a hacker for testing, and after installing each new level of protection, he conducted a test attack. As a result, the webmaster managed to completely secure his site and the hacker could not put it down. But due to the excess of additional filters, each page was loaded for 20 seconds and it was difficult for ordinary users to get to the site.
So attempts to automate protection should be moderate and not reduce site performance.
But still, the webmaster can and is even obliged to take several steps for the basic security of the site or the rented server .
For a conceptual definition of protection methods, it is necessary to evaluate the DDoS itself, to analyze how the attack is carried out. It may be:
-
One subnet
-
One User-Agent
-
One region
-
The same volume of packages
-
One URL, etc.
Therefore, the methods of protection should be carried out according to the result of the evaluation of the previous criteria. For example, subnets require CIDR netmask blocking at the firewall configuration level.
For User-Agents, packages or URLs, blocking at the web server level (by an nginx or .htaccess rule that restricts access to the site) is suitable.
Outbound traffic from one region is blocked using the GeoIP module .
The easiest and fastest method is to block the region if the source of the botnet originates from the same country. If the sources of the attack are globally scattered around the world, leave the site available for some time only for users of your region, for example, for Ukraine.
This will make it possible to reduce the load on the site and take further steps to neutralize the problem.
In addition, you can configure the Fail2ban and Firewall filter: block IP addresses from which requests are made with a certain frequency. But with large botnet networks, this is not effective, since the task is resource-intensive: you need to constantly analyze logs and implement blocking based on a certain criterion.
Among the universal methods of protection, we can advise:
- Cloudflare is a service that provides sites with protection against DDoS attacks at paid and free rates.
- The nginx module — limits the speed of requests in a certain zone.
- Captcha + cookie. Most bots will weed out at the moment of accepting a cookie, the second protective barrier will be a captcha. If both criteria are met - welcome to the site, if at least one is not - limit access to the site.
But you need to understand that the task of installing cookies and captchas should consume as little as possible of the machine's resources. - Setting up a load balancer (Load balancer) in the form of a proxy node that will filter traffic and direct it back to the point (to the server) where the site is hosted.
You should always be ready to migrate the site to another resource by changing DNS, preparing configuration files for the proxy machine, etc. - Response 444. The most effective from the point of view of resource consumption of the server is to return a 444 response from nginx (no response), which, when a suspicious request is detected, resets the connection without waiting for the script to finish.
There are many methods of combating DDoS-attacks, but their use must be done through primary analysis of the source.
Read also: Why Cloudflare is needed and how to connect a site to it
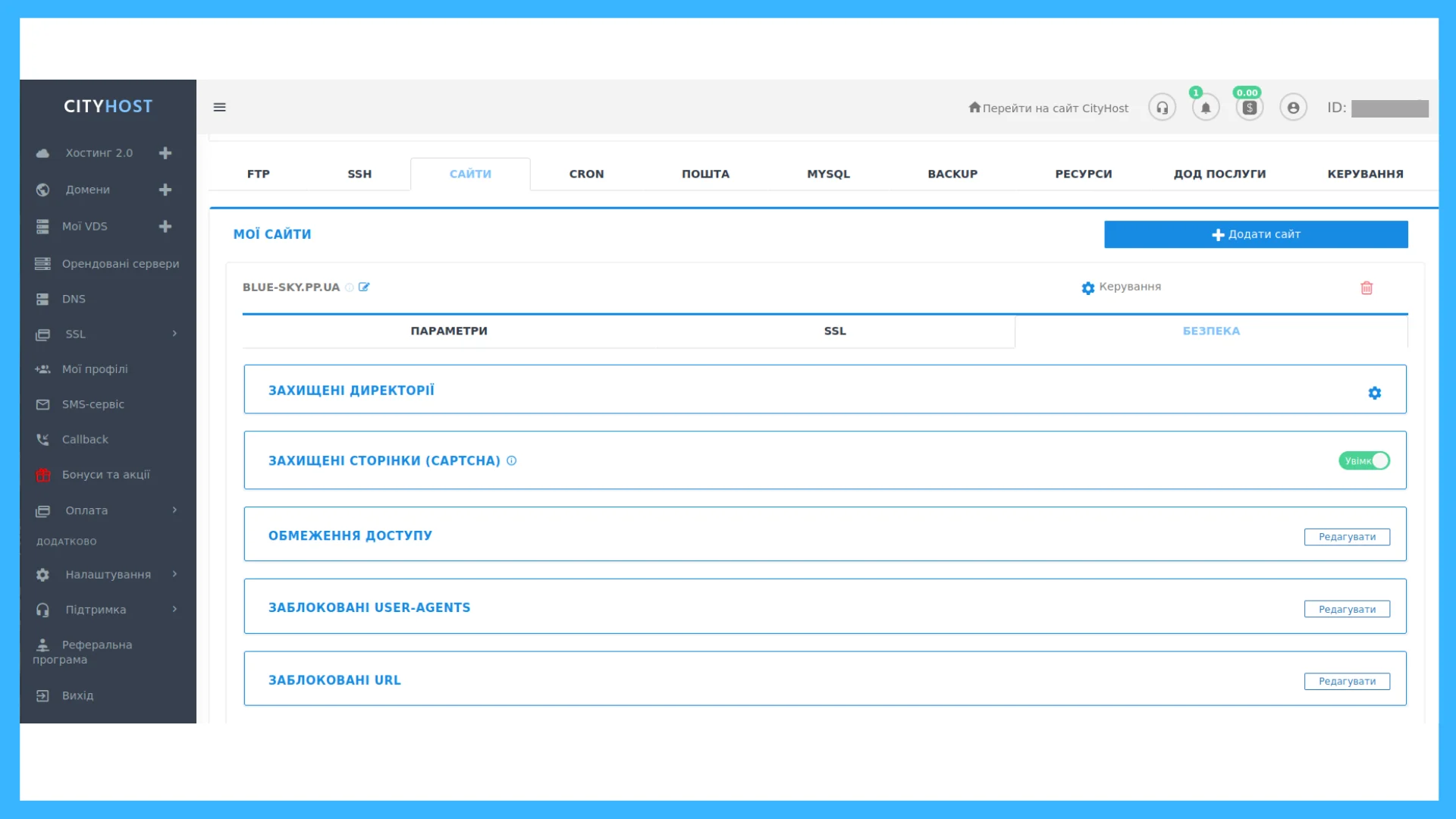
Security tools in the Cityhost hosting panel
In the client dashboard, there are options for primary protection of the site against illegal intrusion and DDoS attacks. You can get to the section by: Hosting 2.0 ? "Management" button opposite the site name ? "Security" tab.
This toolkit is used not only to prevent DDoS attacks, but also to combat other hacking methods.
-
Protected directories. You can set login by login and password for any section or page. Protection can be used for the admin directory, closed sections of the site or even the main page. However, the last option is not always suitable. Then, when entering the main page, each user will have to enter a password - it is, on the contrary, disadvantageous for mass web resources. But for closed corporate forums or sites during the development period, such protection from outsiders is perfect.
-
Captcha Early versions annoyed users by forcing them to choose bicycles and motorcycles, so webmasters often disabled the captcha. In the latest versions, it is enough to check the box next to the words "Confirm that you are not a robot" - such a simple action cuts off bots from getting to the site. The captcha can be installed both as mandatory and as a response to increased traffic from a certain device. If a computer or smartphone receives a lot of requests, it is prompted to pass a check to ensure that it is not part of a botnet. Cityhost sets a mandatory captcha for the CMS admin, so that a bot cannot penetrate it.
-
Access restrictions. Prohibits access to the site to certain IP addresses.
-
Blocked User-Agents. The option can deny access to programs acting on behalf of the user on the network. Most often these are browsers, and User-Agent is a string that identifies each client application.
-
Blocked URLs. Allows you to block suspicious links.
The last three access restriction functions are set manually on a case-by-case basis. You need to monitor site logs and see which addresses or browsers are sending too many requests. Such "guests" are placed on the prohibited list and will no longer have access to the site.
A DDoS attack is a common and destructive technology that is increasingly being used due to the mass migration of businesses online due to the pandemic. Any site can become a victim. Even if it is a small blog, it is difficult to be sure that a novice hacker will not want to practice on it. Therefore, the task of every webmaster is to take care of reliable protection of his site or rented server.