
Most clients, renting hosting from a provider, place on it sites of a completely legal nature - business projects, portfolios, news, blogs. You can publish both a very small amateur site and a professional online store on hosting. The provider will never have any complaints about the quality of the content — perhaps the client is just learning. It also doesn't matter what your site is about, whether it's about pet products, or poetry, or photos of the aurora borealis.
And what about sites that deal with ambiguous topics - is it possible to host, for example, a porn site or organize a financial pyramid on virtual hosting?
There are restrictions on topics and types of content for hosting tenants in the rules of service provision. They are dictated by three main factors:
the need to create a safe workspace for all clients;
technical features of hosting;
Ukrainian and international legislation.
Each provider has a public offer contract, which lists all restrictions and prohibitions on the use of hosting resources.
Let's look at the list of materials that are subject to restrictions on virtual hosting, established by the Cityhost rules.
Financial pyramids, casinos, lotteries
This category includes sites whose activity is based on the possibility of getting players quick and easy money: pyramids like MMM, bookmakers, gambling sites, online casinos, lotteries, etc.
Until 2020, all types of gambling and casinos were banned in Ukraine, now they can operate legally. But in the rules of the providers, this clause will remain in the future, since the neighborhood with such sites carries an element of threat to other customers.
The fact is that sites of this type are often subjected to DDoS attacks, and in addition, they are closely monitored by law enforcement agencies as potentially dangerous.
The provider cannot put at risk all customers who work near a casino or lottery, because in the case of a DDoS, the server may "fall". In addition, if illegal activity is suspected, law enforcement can seize the entire server.
To host their content, organizers of lotteries and other legal gambling games can rent a dedicated server (after granting a license and concluding a contract). In this case, if the tenant has trouble, it will not affect the sites of other customers.
Users, in turn, need to know that legal Ukrainian lotteries and online casinos are hosted only in the .UA domain zone.
Infringing materials and services
This is a fairly broad category of sites whose work causes copyright infringement. Their owners are engaged in the sale of other people's works or developments without paying royalties, the use of other people's trademarks for the promotion of goods, as well as the organization of services that contribute to this activity.
Unfair use of trademarks
A trademark (trade mark) is a registered object of copyright that contributes to business recognition, the formation of the company's image and its promotion on the market.
But why spend effort on creating your brand, if you can use an already known name? This is what unscrupulous website owners think, using names, logos, corporate colors, designs or domain names to indicate their product so similar to well-known brands that they are easily confused.
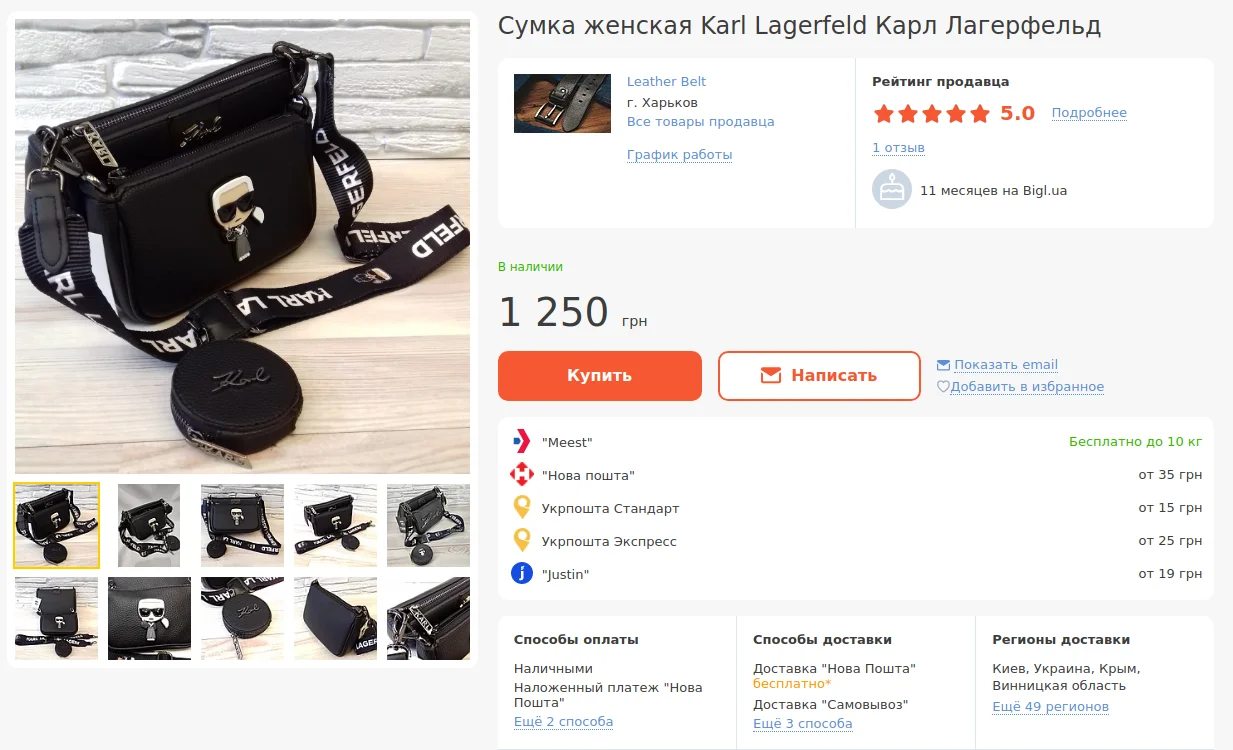
It is also illegal to sell, through the site, goods that bear a name or logo that sounds or looks similar to a well-known trademark. A legendary example of such copying can be considered the once mass sneakers "abibas" and cheap bags with the signature print of Louis Vuitton or Dolce & Gabbana.
That's how easy it is to buy a bag with Karl Lagerfeld's name in Ukraine for 1,250 hryvnias, despite the fact that a similar clutch in the original costs about $250.
Pirated content (warez)
The term warez in the Western world refers to any pirated content. In "runet", this word refers only to hacked software that is distributed without the permission of the copyright owner.
Copyright objects distributed by third parties unrelated to the creation and legal sale of the product belong to pirated content:
Movies
Books
Musical works
Images (photos, illustrations)
Software
Computer games
In order for authors and developers to earn money, their works are distributed through contracted agencies and sites. For each download or view, the user pays a small amount, a percentage of which is accrued to the rights holder as a royalty. The owner of copyright can be not only the author, but also the organization that purchased the rights, as well as the heirs.
In the Western world, you are unlikely to be able to listen to a song or watch a movie without paying - there the system works clearly. Our fight against pirated content is just getting started, encountering resistance from users who are used to everything free.
For us, piracy is so common that the organizers of the sites are not ashamed to call them something like "Kinokrad". It is not for nothing that different versions of the online cinema are placed on a dozen domains - the resource is periodically blocked, but it is reborn like a phoenix from the ashes.
Torrent and crack services
This is already a toolkit for the distribution and use of pirated content. Torrent trackers are services that create a network of computers that share files with other users. Even if the content is obtained for a fee, its further distribution is already a violation of copyright. This is exactly what happens on torrents.
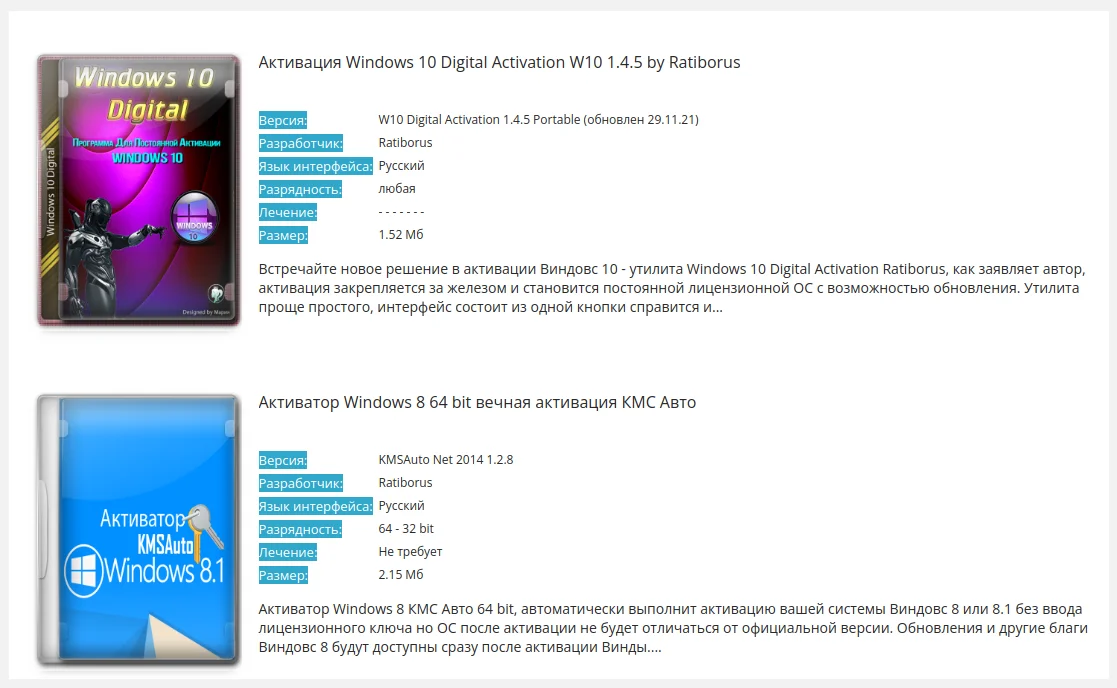
Crack services (also called "cracks") are key generators for cracking software. They are used to install paid programs or operating systems for free, which is also a violation of copyright and property rights.
Not all users understand that they are committing an illegal act by downloading such a program. Hacker suppliers modestly call them "activators" and attach photos of licensed software boxes, lulling users' attention.
Sale of information obtained illegally
Not only the content of the content on the site is important, but also the methods by which the information is obtained. This is a separate section of violations that not only affects copyright, but also violates other laws.
Illegal methods of obtaining information are downloading with the help of special programs or services to bypass blocking designed to prevent data from being copied; blackmail and extortion, server hacking, industrial espionage, etc.
Sites for the distribution of pornography
Any content aimed at selling sex is prohibited for publication - pornographic films, escort services, prostitution, webcams, as well as shops that sell "adult toys".
Political propaganda
Yes, politics is also on the "black list". Political campaigning uses not always honest methods of influencing the electorate, competitors "pour mud" on each other and may even make extremist appeals. That's why all political races have been moved to mass media platforms, which are responsible for spreading false information.
Advertising and sale of narcotic substances
The legislation of most countries prohibits the production and distribution of drugs. In Ukraine, this applies to all types of light and hard drugs — from marijuana and smoking mixtures to LSD and cocaine. The same applies to the seeds of plants that contain narcotic substances, as well as medicines that are used for narcotic intoxication and are sold only by prescription.
For this reason, any advertising activity related to the sale of these goods, in particular on the Internet, is prohibited.
Malicious software
Malware aims to illegally infiltrate and control users' devices without their knowledge, scan site code, collect confidential data without authorization, damage site code, and many other purposes, mostly fraudulent.
Viruses and scripts that perform actions without the user's knowledge
Viruses are malicious code capable of self-replication and spread over the network. There are many types of virus code that can penetrate websites, computers, servers and gadgets and cause irreparable damage.
Read also: Viruses on the website - how to find them and protect yourself from infection .
Malicious scripts can work independently on the user's device, which he will not even know about: mine cryptocurrency, participate in DDoS attacks, transfer data from the computer to fraudsters, etc.
Parsers and other lace scanners
Parsing is the automatic collection of information from websites. It is often used to monitor competitors — they collect data on prices, popular products, and reviews on websites. In general, parsing is not prohibited, but this method is also used for illegal collection of confidential data, content theft, and DDoS attacks. It is an ambiguous tool that is often used for nefarious purposes.
Network scans collect different types of data and work in different ways. Some follow links, others pick up passwords, and still others check sites for vulnerabilities. They not only endanger the information security of sites, but also create a serious burden on them.
Services that distribute malicious software
Malicious programs are not transmitted by the power of thought - they have to be downloaded somewhere. There are special sites where you can find malware. Of course, such sites are illegal, and using the tools downloaded from them is a violation of the law.
Sending spam
When using the provider's mail services, it is prohibited to send mass spam. It is worth noting that the restriction applies specifically to spam and does not apply to business mailings to customers.
You can learn how to distinguish them from the article "Why it is better to use a special service for mailing".
Proxy servers and anonymizers
These are special services that help the user hide his IP address and visit sites anonymously. Proxy servers also have completely safe tasks — protecting the user from hacker attacks, speeding up the connection, and caching data.
But mostly, these services are used to bypass blocking, visit prohibited sites and help fraudsters to operate without revealing their location.
Phishing sites
Phishing is the creation of copies of well-known online stores, advertisement sites, payment systems and other web resources on which payment transactions are carried out. This is a simple and cunning fraud scheme that lulls users' vigilance and forces them to leave their card details on malicious sites, after which money disappears from their accounts.
Fraudsters can use the names of well-known marketplaces, TV channels and even disguise themselves as government services. Their goal is to create trust in the user so that he voluntarily enters confidential information on a "scam" site.
Sites related to gaming
You will be surprised - are games illegal too? Hundreds of online games are sold on the same Play Market. What could be wrong with strategy, chess, or puzzle-building?
In this case, the ban is more likely due to technical reasons. At a certain point, the providers realized that the largest number of DDoS attacks were carried out on game sites. It is unprofitable for ISPs to host a couple of game sites, and then constantly fight with "ddosers", that's why this ban exists.
However, game developers and distributors should not be upset - for this purpose, you can rent VPS hosting .
Using the file system
Only site files can be placed on hosting. It is not allowed to use memory to store:
file archives, images, videos and other files that are not used by the site;
databases that are not used by the site or are managed through a remote connection not from the client's hosting;
website backups (more than one week);
non-working cache files that are not automatically deleted.
There are also limits on the size and number of files that can be stored on the system.
These are the main types of materials subject to restrictions. You can familiarize yourself with the detailed list in the "Rules for using services" .
How to file a complaint on the site?
If you saw unacceptable content on a site hosted by Cityhost.ua, write about it to technical support at support@cityhost.net.ua and we will definitely take action.
To find out on which hosting the site is located, use the Whois service. In the Registrar section you will find the name and address of the provider. Anything marked with the word abuse are contacts for sending complaints.
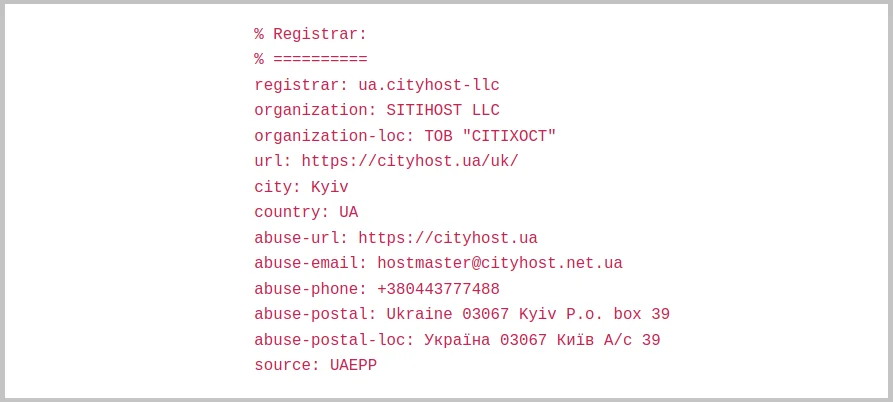
There are also other ways to find out the hosting of someone else's site - you can use them if the Whois search did not give results.
Upon receiving a complaint, the provider forwards it to the client and offers to eliminate the violation. If requests are ignored, the hoster reserves the right to temporarily or permanently block the site.






