.webp)
- What is a Firewall and How Does It Work
- Types of Firewalls
- How to Configure a Firewall on Your Computer or Server
- How to Configure a Firewall on a Virtual Server
- Firewalls for Websites: Web Application Firewall
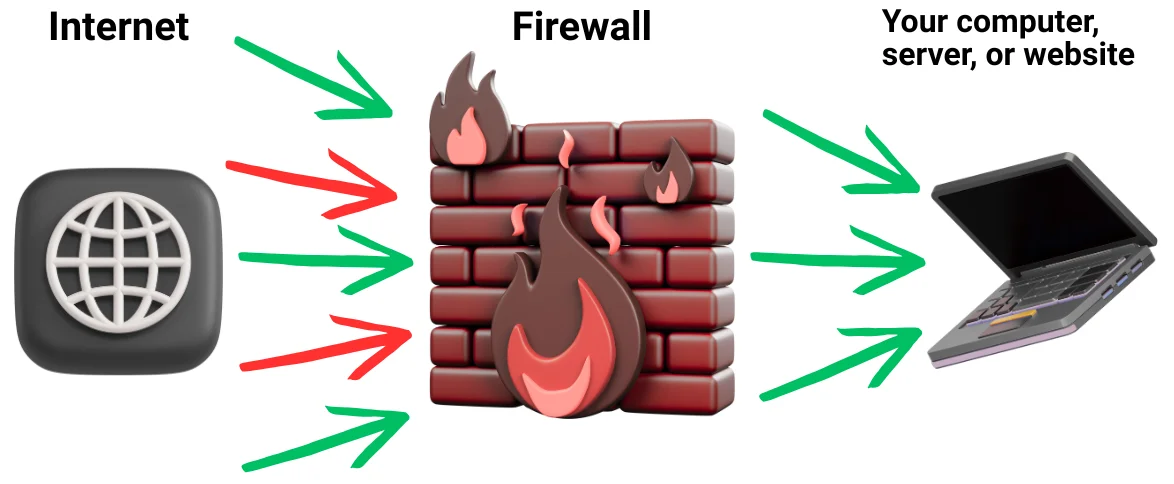
Cyberthreats increase every year, and not only large corporations but also ordinary users face risks of hacking, data theft, or unauthorized access. One of the oldest and at the same time most effective security tools is the firewall. Its task is to control all incoming and outgoing traffic, creating a “boundary” between the safe environment and potential external threats.
What is a Firewall and How Does It Work
A firewall is a system that filters network traffic according to predefined rules. Simply put, it analyzes all connection attempts to a computer or server and decides whether to allow or block them.
The principle of operation can be compared to a security guard at the entrance of a building: he checks visitors’ documents and only lets in those who meet the requirements. In the digital world, these requirements are network protocols, IP addresses, ports, and types of connections.
How it works in practice:
- Incoming connections. If someone from outside tries to connect to the computer on a certain port, the firewall checks whether such a connection is allowed.
- Outgoing connections. Applications on the device are also monitored. For example, if a virus attempts to send data to a remote server, the firewall can block it.
- Logs and monitoring. Many modern systems keep records of all access attempts, which makes it possible to detect suspicious activity.
Why is a Firewall Needed?
It is used to:
- restrict unwanted external connections;
- protect personal data from theft;
- prevent the spread of malware within a local network;
- control which applications are allowed to access the internet.
Read also: Server health monitoring, backup and data security - what hosting customers need to know
Types of Firewalls
Depending on the area of application, there are several main types:
- Hardware firewalls. Separate devices installed at the network boundary (for example, between an office network and the Internet). They are capable of handling large volumes of traffic and are often used in large companies.
- Software firewalls. Installed directly on a computer or server. A classic example is the built-in Windows Defender Firewall. They are well suited for individual users and small businesses.
- Combined solutions. For example, routers with integrated firewall functions. This is a compromise between simplicity and functionality.
Firewalls are also distinguished as network firewalls (which protect an entire local network) and personal firewalls (which protect a specific computer or server).
How to Configure a Firewall on Your Computer or Server
Firewall configuration depends on the operating system. Usually, it is enough to allow trusted programs to work and close all unnecessary ports.
Firewall in Windows
Windows has a built-in automatic firewall. In Windows 11, this tool is called Microsoft Defender Firewall, as Microsoft is gradually phasing out the old name Windows Defender Firewall, which you may still see in earlier versions.
How to change the settings:
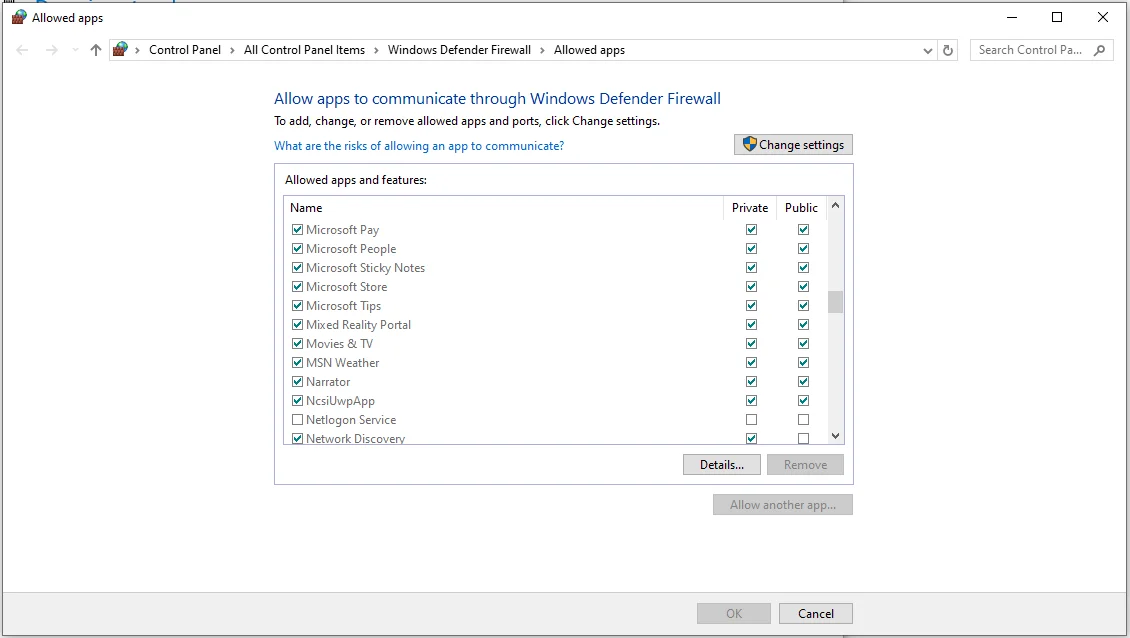
- Open Control Panel ⇒ System and Security ⇒ Windows Defender Firewall (Windows 7/8/10) or Settings ⇒ Privacy & Security ⇒ Windows Security ⇒ Firewall & network protection (Windows 11).
- In the menu, select “Allow an app through the firewall” (or find this feature via search). Check the boxes for programs that require network access.
A green checkmark in the checkbox means the application is allowed to connect to the Internet; if it is unchecked, access is blocked. For convenience, settings are divided into two types: Private network (home or office Wi-Fi) and Public network (café, hotel, airport). This allows you, for example, to grant a browser access in any environment but restrict work programs or services to a private network only, which increases security.
Most users can manage with simple settings — just checking or unchecking the boxes next to the desired program.
The firewall also has advanced settings with detailed rules for ports, protocols, and IP addresses. These are more suitable for system administrators and are only required in special cases. If you are a beginner, basic settings are usually sufficient.
Example: Allow access to port 3389 (RDP) only from specific IP addresses, blocking all others.
You can learn more about firewall settings in Windows here.
Firewall in Linux
In Linux, iptables is most often used, or a more user-friendly frontend called UFW (Uncomplicated Firewall).
Basic UFW commands:
- sudo ufw enable — enable firewall
- sudo ufw status — check status
- sudo ufw allow 22/tcp — allow SSH
- sudo ufw allow 80/tcp — allow HTTP
- sudo ufw allow 443/tcp — allow HTTPS
- sudo ufw deny 21/tcp — deny FTP
- sudo ufw disable — disable firewall
These rules help quickly set up basic server protection. For more complex scenarios, firewalld or other modern firewall management tools are usually used, which are available in various Linux distributions.
How to disable a firewall?
- Windows: Control Panel → Windows Defender Firewall → Turn Windows Defender Firewall on or off. Here you can temporarily disable it for private or public networks.
- Linux: Command sudo ufw disable.
Important: A firewall should only be disabled during testing or diagnostics. Permanent disabling poses a serious security risk.
How to Configure a Firewall on a Virtual Server
For virtual servers (VPS/VDS), a firewall is especially important, because the server is constantly accessible from the Internet and becomes a target of automated attacks — from port scanning to password brute forcing and exploiting vulnerabilities in services. Most hosting providers offer basic protection at the infrastructure level, but you should additionally manage access yourself. In the VPS control panel, tools for creating firewall rules are usually available: you can open or close ports, restrict access to SSH/RDP only from specific IP addresses, and block all other connections.
A detailed guide explains how to configure a firewall on a virtual server step by step in the client area.
Examples of settings:
- allow only web services: 80 (HTTP) and 443 (HTTPS);
- open SSH (22) only for your IP address;
- block dangerous services (Telnet, FTP).
If you open access to all ports, the server will quickly become the target of password-guessing attempts and botnet attacks. Even simply blocking unnecessary services significantly reduces the attack surface and makes the system much more resilient. Therefore, configuring a firewall is not a one-time action but an ongoing process of control and optimization.
Firewalls for Websites: Web Application Firewall
A classic firewall protects the operating system and network services, but this is not enough for websites. Web applications are attacked through SQL injections, XSS, brute force, or DDoS. For this, there is a Web Application Firewall (WAF) — a specialized firewall that analyzes HTTP(S) requests and blocks malicious ones. On hosting, the basic firewall is configured by the provider. The client usually can only:
- block IP addresses/subnets;
- set up a WAF through a module or service.
Types of WAF Solutions
- Cloud-based:
- Cloudflare — protects against DDoS, SQLi, XSS, and adds caching.
- Sucuri — specializes in protecting WordPress and other CMS platforms.
- Imperva — enterprise-grade protection with advanced analytics.
- Server-based:
- ModSecurity — an open-source module for Apache/Nginx that works based on OWASP Core Rule Set rules.
- CMS Plugins:
- Wordfence (WordPress) — comprehensive protection (WAF, antivirus, monitoring).
- iThemes Security (WordPress) — basic WAF functions and enhanced security.
How it works: WAF checks each request and, if it detects an SQL injection attempt or other suspicious code, blocks it before the site processes it. This reduces the risk of hacking even if there are vulnerabilities in the CMS or plugins.
Protection against brute-force attacks on WordPress: the Wordfence plugin limits the number of login attempts and blocks unauthorized attacks.
A firewall is the first line of defense, without which secure work with the network is impossible. On a computer, it blocks unwanted connections; on a server, it allows only the necessary ports to remain open; and for websites, an additional WAF protects against common attacks. Configuring a firewall takes little time but significantly reduces risks for both users and businesses.