
Today, when the bulk of computers work through hosting, use various programs and mask the weekend, additional online support is necessary. From English, proxy is translated as "trusted person", that is, the connection between the consumer and the end point.
There are two types of them:
- Local Make it possible not to overload the resource often.
- External. Acceptable for everyday private use, which ensures high speed of material processing and preservation of anonymity. The biggest plus is quick access and ease of use.
What is a proxy server?
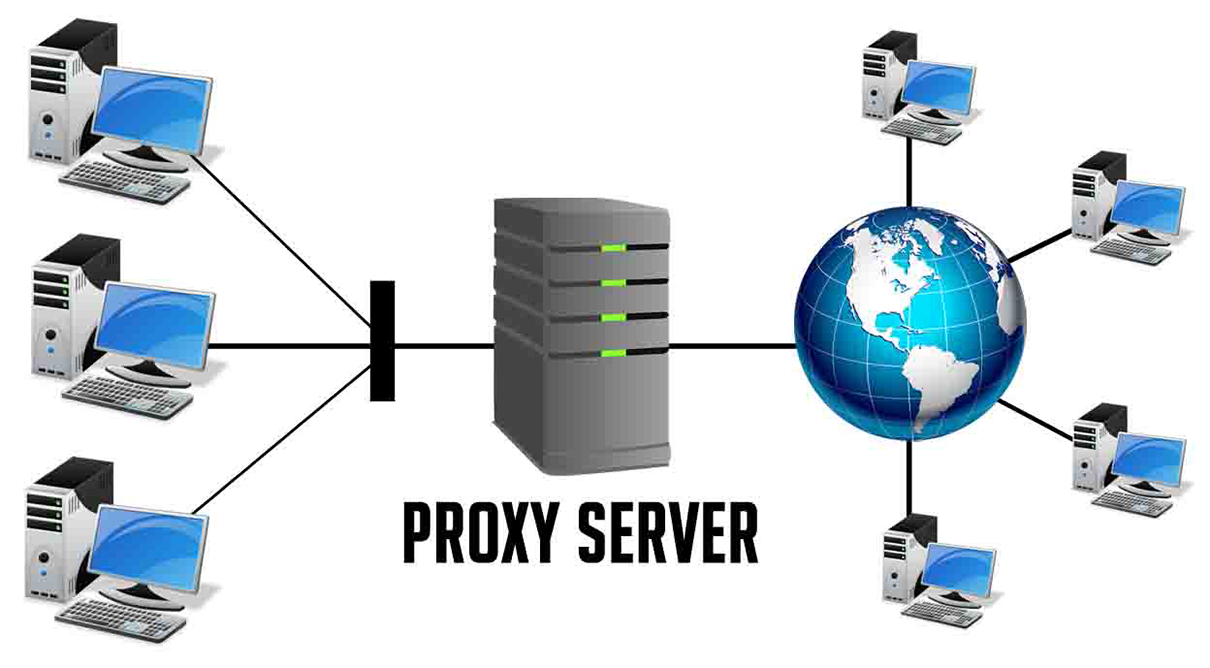
With billions of requests per day, a content distributor is needed for proper routing to a destination with a separate IP. Proxy settings work as a transmitter, there is no direct contact between the personal personal device and the target. A similar connection is necessary for two incompatible systems.
It does not matter what gadget the client uses, mobile or stationary, the service provides for the use of the filtering function and the provision of complete anonymity. There are two types of proxy server addresses: forward and reverse. The first protects as much as possible from external influences from the Internet. The second says to use protection with a higher device.
Possible types
Direct is a simple intermediary between a personal device and the global network. Reverse connects a global network with a group of similar devices, their task is to convert protocols from one type to another for networks that use different algorithms, and to serve as a gateway between a local device and the Internet. Paid or free server proxies have a large set of features. They are also called "public" because anyone can use them.
Who needs it?
First of all, users for whom it is important to keep the complete confidentiality of the IP address. Modern web services and online resources collect a lot of personal information about network users: which sites are clicked, links, locations, preferences in the network. To maintain personal security, you can use the available public option and get the service for free.
Security guarantee
With the help of the anonymizer, complete confidentiality and inaccessibility of the personal IP address is ensured, instead of which a common identifier is visible, which allows to preserve the anonymity of the user. This is important because the address determines the location and any personal data that can be used in fraudulent schemes. Even free server proxies in Ukraine allow you to hide geolocation and expand the possibilities of using access to the network. For example, by hiding your location, you can connect to online channels outside your country.
Content loads faster
The time reduction is related to the data caching process. All accesses to online platforms are saved automatically, which saves time for displaying the page. It is necessary to take into account that the page must already be loaded. Otherwise, it will take time for the initial download, but then the process goes faster.
Weeding out bad sites
Using an intermediary allows you to filter out web platforms that may carry a threat. Blocking of malicious content is carried out by the administrator, who determines the degree of danger of the link. Also, the proxy server serves as a kind of barrier. If the user goes to a broken link, it is not his personal device that is exposed to infection, but the intermediary. The signal will be resource blocking.
Proxy server, list
You can find the right platform that cooperates with hosting from almost any Internet provider and use open access. The lists are freely available on the Internet. Geolocation is not limited. Select the required data and enter it manually in the search window of the browser and the proxy service of the operating system.
Read also : The main permalink exchanges .
Where to start?
You can start work immediately after the address has been chosen. Settings are set in the operating system and in the browser. Direct implementation into the system allows it to be used by all programs, and installation in a browser gives access only in this browser. The first option makes it possible to manage all traffic through the server. The second allows you to control a specific browser, the others work in normal mode. You can use one or several proxies for different programs.
Step-by-step instructions for Windows 10 users:
- Enter the word "proxy" in the Windows search bar.
- At the bottom, activate the start of the server.
- According to the information from the provider, enter the port and service data. All this can be found in the documents or on the provider's website.
- It remains only to save the settings with a special button. After these manipulations, you should notice an acceleration in work and loading.
- If the use of the proxy server is no longer relevant, it can be deactivated using the corresponding button.
- Check the connection via IP address: it will change depending on whether the proxy is enabled or disabled.
Windows 7, how to make changes:
- Actions are performed on the control panel.
- Select network settings and browser properties in the menu.
- In the "Internet Properties" window, connect to the local network.
- The procedure allows you to configure various configurations, the operating system automatically selects the optimal scenario, or the user makes manual settings.
- For manual intervention, you need to remove the flag from auto detection to avoid errors.
Why is this necessary?
An intermediary between the client and the underlying web platform is required to obtain a particular service. For example, you want to go to a news resource. The anonymizer accepts the request and goes through the following stages:
- The local cache is checked for certain information. With a positive result, the client receives an internal link, global interpellation is not made.
- If there is a negative result in the internal storage, the search continues on the Internet. For security purposes, a special common ID is used, not a personal user ID. Anonymizer acts on behalf of the client, creating a special address. Only after finding the required content is the connection made with the client's account.
Four aspects of this service: creation of cache files, passing the filter, control over the ability to receive information and ensuring confidentiality. There are certain parameters for the filter. All information is sorted according to special characteristics, the necessary resources are stored in the buffer, the load is distributed between servers to ensure smooth operation and high speed, it creates a barrier for the influence of malicious sites and cyber attacks on a personal computer.
Read also : What are keywords .The difference between an anonymous proxy server and a regular one
When searching the network through normal traffic, all requests are sent directly from the user's computer to the target medium. The requested data is redirected directly to the user's PC in the form of a link to the site. In this regard, the user must provide all his personal data so that the answer is returned directly to you. Data about you will be saved, as a result, the information is no longer confidential and can be used by advanced fraudsters.
Features of the anonymous proxy server
When using an anonymous login, privacy is completely protected from third parties. Instead of a personal IP, an artificial temporary address is created, which sends a request to the network. After responding to the client, the user's data is not stored, which ensures complete confidentiality. Only Anonymizer address data is available to the operator. On the other hand, information is also blocked and only the path of the request from the user's computer to the intermediary is visible. the result cannot be tracked.
Read also : What is hosting .Anonymous access is both paid and free. You can find many different high-quality options online. Applications cache requests for content, which affects the speed of information search. You can work through a proxy server without installing additional software, there are many free versions available. Thanks to address masking, traffic is accelerated and data security is ensured. Only high-quality and expensive virtual private networks provide a full guarantee of anonymity and high speed of request processing.
Nuances of working through a proxy server
To start work, an address from the proxy list is entered into the operating system. The same information is entered in the browser. Almost all browsers launch the information automatically after the first entry. If you noticed that your Internet browser did not save the link, you need to manually go into the settings and correct the error so that all programs are automatically redirected to the computer in the future.
How to work with Google Chrome?
- In the upper right corner of the browser, find the "Settings" option.
- You need to make changes in additional settings.
- In the properties of the Internet there will be a link to the local network. Enter the required address to activate the proxy server.
Features of settings for Firefox:
- The menu window opens in the upper right corner by clicking on the check mark.
- In the "Additional" option, there will be a link to the network and general settings.
- The address and port are entered in the manual settings of the service and HTTP. All information can be found in the proxy server list.
- After use, everything must be removed. If the proxy server ceases to be active or access to it is blocked, you cannot use the Internet.
Problems and errors that may occur during operation
There are a number of reasons why errors occur when using intermediary servers specifically.
- Platform overload. This applies mainly to the free versions. They are used by a huge number of users. As a rule, the amount of traffic cannot cope with the number of requests and the resource starts to reload. The user perceives this as a failure in the system. Often clients prefer to use other services.
- The ability to log in may be blocked if the resource has been disabled or deleted altogether. There are usually two reasons: a technical failure or the provider's failure to comply with the terms of payment. You need to use another site.
- If the IP owner changes, it will be impossible to connect. The problem is solved by entering the required configuration in the browser or system settings.
- An error during data transfer during connection due to incorrect settings of the proxy server itself. You can fix it by contacting a special technical support service. Specialists will check anonymization settings, access to the resource, possible errors in entering information, addresses and network ports.
Important information for those who have chosen a proxy.
- The use of an intermediary server gives the user a full guarantee of keeping personal data confidential. But if you set yourself a goal and have sufficient knowledge and skills, you can get access to information by bypassing the anonymizer.
- To prevent this from happening, it is important to very carefully analyze all the features of a proxy server before making your final choice on one of them. Remember that the provider has access to the personal device, and accordingly to the data. This is possible if access is not via HTTPS, but HTTP. Then your actions can be easily traced. Another danger is the administrative service operator. It can block access without explanation or warning.
- Sometimes the bandwidth is limited directly by the provider. In this case, you need to make sure that you have high traffic and the problem is not yours.
- There are so-called "transparent" servers. They are specially used by providers. With such authentication proxies, the software product will send all identity information to the end resource. The method is used to improve traffic.
- It is better to buy the service rather than use the free access. Almost 80% of open accesses do not use the HTTPS protocol, which reduces guarantees of security and protection against cyber attacks. Some free resources independently change the codes and markup, putting the user to sleep with advertising.
- In order not to make a mistake with the choice when buying, check the reliability rating. Make sure your provider uses a verified hosting.
When weighing the capabilities of an anonymizer and a VPN, check the protocols. In any case, when choosing between a dedicated storage and an anonymizer, carefully consider the issue of security and the level of protection offered by the provider. You can order a working proxy server, high-quality hosting , and register a domain at the CityHost company. We provide you with the possibility of full control over your resource, high-quality technical support 24/7, a guarantee of complete security.








